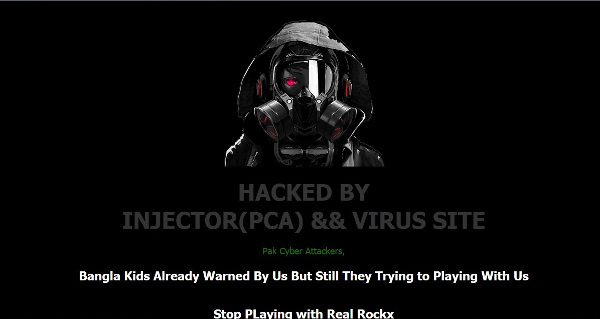
If your business relies on your website for even part of your lead generation or sales, seeing your Home Page turn into something like this could be your worst nightmare come true. It can be very tempting to panic at the sight of something like this! Panic is exactly what the hacker wants however. It’ll paralyze your response and delay getting the hacks taken down and your proper site restored to it’s fully working condition from before the hack.
The cover image is a screenshot of a real hack I encountered last summer. The owners of this site relied exclusively on this website to process all orders, meaning as soon as this happened, they couldn’t sell anything. The good news is we were able to restore their site to full working order, removing all traces of the hack and get their business back online.
What Do I Do If My Site Is Hacked?
If you run into something like this, the first step is to call your Web Hosting company and report your site as hacked. They can advise you on steps to take to recover your website as well as help you lock access to your site to protect your legitimate visitors from getting hurt by the hack, such as the hacked site installing viruses and other malicious software onto their computers.
The next step is to check all your company computers and servers for any signs of infection. (Follow the steps in this article or consult a computer security specialist to do this). If you visited the site on your company computers, there’s a good chance this site did at least try to install something malicious on your computers or company network. If your company already has good security in place for your computers there’s a good chance any attacks on your computers may have been blocked by your security software but I wouldn’t assume this is the case. I would still look just to be sure.
While your own computers are being checked out, you can either:
- Follow the recovery instructions your Hosting service provided you with.
- Follow the steps in this guide created by Google to help website owners in recovering from a hacked website (https://developers.google.com/webmasters/hacked/).
- Consult a network or website security expert to help you recover your site.
Of course, most hacks are not so obvious as the one in the screenshot above, so you do need to do your due diligence in making sure your website hasn’t been hacked without you even knowing it.
Detecting A Hacked Website
While the best hackers with the largest budgets can leave no noticeable trace of their activities on your website, those types are usually military or government espionage hackers, so they likely won’t care about infecting your site, your computers, or your customer’s computers.
The main hackers you’ll have to worry about are:
- Professional hackers who want to use your site to find valuable info they can sell, either directly or by infecting more computers to aid in future attacks on bigger targets. They can be skilled or rely on pre-packaged attack kits. Since they’re mainly motivated by profit, if your site’s harder to hack then the perceived value, these kind will likely look for more profitable victims.
- Revenge hackers are someone who wants to get back at you for something. They could be a disgruntled ex-employee, customer or vendor who feels you did them wrong and want to get even. They’re less likely to be skilled hackers then the pros, but can be just as dangerous or even more dangerous in their own way. They’ll be the most determined to break in and may attack your site relentlessly for weeks, months or even years.
- Status hackers are probably the least threatening. They’re usually looking for the bragging rights to claim they successfully broke into something, but aren’t necessarily looking to cause any harm. They can expose vulnerabilities to other more dangerous hackers in their bragging however and that can be a huge problem.
So with all that in mind, what signs will hackers likely leave behind that your site’s been hacked? The most obvious signs can be that your search engine has flagged your site as hacked while indexing it, or that your browser or security software warns you of malicious content on your site when you go to visit it.
Other less obvious signs can be if your site starts downloading or installing software on your computers when you visit it, starts redirecting you to a strange website or searches for your company/website on search engines turning up strange results.
A cleaver hacker can attempt to hide strange redirects from you by making them happen only when arriving from specific sources like a search result, so you should arrive at your site the way a new visitor might, by using a search engine to look for this.
Customer feedback can also be a great warning sign of a possible hack. If you’re getting complains of an any of the above symptoms, strange error messages or anything else out of the ordinary, these can also be signs of a hack. Some can also be signs of a programming bug, but either way you’re going to want to get it fixed.
For more info on what signs to look for on a hacked website you can see this article published by Kaspersky on the subject.
After the Recovery
Once you’ve gotten the hacked content out of your site and recovered it back to normal, you may think your job is done. It’s not. There is still 2 critical steps to take:
- Find out how your site got hacked in the first place.
- Fix the vulnerabilities the hackers used to hack your site.
The first part really should start with taking a look at all user accounts associated with your website.
That means examine:
- If you use a CRM system (such as WordPress) take a close look at what user names and passwords you’re using, especially for any “admin” accounts. With this level of access, an attacker can upload malicious files and insert malicious code into your site.
- Logins to your hosting account (eg: Hostgator, GoDaddy, etc). An attacker can use these logins to gain access directly to your databases and file system to upload malicious content, or inject malicious code into your site, as well as manipulate your “DNS” settings, meaning they can send traffic to other sites that should be going to your site or do all kinds of harmful things. They may even gain access to your credit card details from here, depending on your host!
- All “FTP” (stands for File Transfer Protocol) accounts associated with your account. Hackers who gain access to this, can directly access your website’s file system and edit your files directly, as well as upload their own files, and download your files too. Most people tend to ignore these accounts too, as they seem too technical and intimidating to look at.
- All email accounts associated with any of the above accounts. These email accounts, if hacked, can be used to do password recovery, so even if you do change all your passwords to something more secure, the hackers can just click that convenient “forgot password” link and get right back in any time they want. By making sure your email accounts have the strongest passwords possible and using the best anti-hacking tools your email provider has to offer, you can remove this easy hack at least.
What’s Needed for a Good Login?
User Name
This is one half of the info needed to log into an account, so if you have the option, make it as hard to guess as possible. Don’t use anything obvious like “admin”, your company name, personal name, or that of anything that’s publicly available. These will be the first things a hacker will try.
Password
This is the other half of the info needed to access your accounts. This one takes a bit more explaining though. What I said about User Names applies to passwords as well, and is even more critical, especially for those accounts where you have no control over your User Name, such as if it your forced to use your email address.
A strong password first and foremost, needs to be something that a little research won’t reveal. So using your street name, pet’s name, or anything else that can be found with a little research is a very bad idea! Hackers will test these password possibilities first.
A password also shouldn’t use only words right out of a dictionary. Failing obvious personal info, hackers will next try every word in the dictionary, and all common variants, such as capitalization, misspellings and other variants.
A good password should consist of a combination of capital and lower case letters, numbers and special characters such as punctuation, marks, #, @, %, etc. Mix the locations of these around, and use phrases as the starting point for your password. Mix in the numbers capitals and special characters more or less randomly.
A common mistake is to use a simple word or phrase, then just throw in a token capital letter at the beginning or end, and a token number or special character at the end to “trick” any password complexity screens into accepting an easy password. Hackers love this trick as it makes guessing your password and hacking your accounts easy for them.
Why make things easy for a criminal who wants to do you and your business contacts harm? Make things as hard as possible and most will give up on you or waste their efforts on something they’ll probably never penetrate. If you are worried about forgetting your password, remember that you can recover it if that happens, and you can keep a password written down in a secure location in for a master email account (the email account your other accounts eventually trace back to for password recoveries.
Keep All Software Your Site Uses Up-To-Date
If you use any pre-programmed software on your site, such as running it on WordPress, or calling upon any pre-coded packages for a custom coded site, make sure you update them whenever a new version comes out. These updates fix not only bugs, but also security weaknesses a hacker could use to break into your site.
These are all steps you should be able to take yourself, however even with these steps, a determined hacker with the right skills or tools can bypass all this. So I recommend also consulting with an expert who can run tests and implement fixes to close down other holes in your site’s security to make you even more secured against hackers.
These steps will help ensure the hackers don’t get back in, and you can bet that if they got in once, they’ll try again. They’ll see your site as vulnerable and continue to target it.
Of course, while recovering your site from a hack necessary when it happens, the better course of action is to be pro-active and take steps to prevent your site from getting hacked in the first place. Maintaining regular updates and keeping all logins secure will help, but there is more you can do. We’ll get into preventative security tips in our next article.
If you’ve had any experiences with getting hacked, have any questions or feedback, feel free to leave a comment below. If you think your website may have been hacked, don’t hesitate to contact me ASAP.